Quantum networking is a technology that promises to enable tamper-proof communication over optical networks. Synthetic-diamond chips with so-called silicon-vacancy centers are a promising technology for quantum networking because they’re natural light emitters, and they’re small, solid state, and relatively easy to manufacture at scale. But they’ve had one severe drawback, which is that they tend to emit light at a range of different frequencies, which makes exchanging quantum information difficult.
Last year, members of Amazon’s AWS Center for Quantum Computing, together with colleagues at Harvard University, the University of Hamburg, the Hamburg Centre for Ultrafast Imaging, and the Hebrew University of Jerusalem, demonstrated a technique that promises to overcome that drawback. They will present their results in a forthcoming paper in Physical Review Letters titled “Optical entanglement of distinguishable quantum emitters”.
The first author on the paper, David Levonian, a graduate student at Harvard and a quantum research scientist at Amazon, answered three questions about the research for Amazon Science.
Q: What is quantum networking?
David Levonian: A quantum network is a technology that allows you to send quantum bits over fiber optics using single photons — single particles of light. The original interest in it is that by sending these quantum bits between users, you can generate cryptographic keys in a way that's secure.
As you're able to get higher bandwidth and throughput through these things, you can do really cool stuff. Say Amazon, for example, has a quantum computer, and you don't have one, and you'd like to run computations on Amazon’s, but you don't want to reveal what data you're actually using or what programs you're running.
It turns out that if your computer can connect to a quantum network, without much special hardware on your side, you can actually send programs and data and have Amazon execute them and then come back to you with a guarantee that nobody looked at any of the stuff that you were doing.
People are trying to build these networks in a variety of ways. What we work on specifically is a hardware implementation that's built on these little chips of diamond. The diamond is made of a bunch of carbon atoms. Pluck out two of those and add a silicon atom. Now there are two holes in the crystal, and the silicon sits in between the two holes. It brings an extra electron, and that electron can absorb light, and it can also store quantum information.
You can use these silicon-vacancy centers as storage registers — people call them quantum memories — to catch light and route it and do quantum operations on it. And you need that quantum memory to build the quantum network for these security applications. People also use trapped atoms or ions and other stuff, but for those you need really big machines. Our system is a little chip, which is pretty cool.
Q: What problem does your new research solve?
DL: One of the current problems with silicon-vacancy centers is that they're not as uniform as other quantum network hardware that people use. If you have a big network of these things, you want them to communicate between each other with light. And one of the things about silicon-vacancy centers — and actually most of the defect centers in crystals — is that one silicon atom doesn't always emit the same wavelength of light that another defect can receive, so you have trouble matching up your different bits. And that's been a big barrier to actually building these things.
What we came up with is a way of making silicon vacancies that emit light at different wavelengths talk to each other. It’s based on a thought experiment from the ’90s called a Elitzur–Vaidman bomb tester. The motivating idea is that there might be a bomb somewhere, and it's so sensitive that even if you hit it with a single particle of light, it's going to go off. So you want to test whether or not it's there without hitting it with any light at all.
It turns out there's a quantum-mechanical way to check whether there's a thing blocking light at a position without having any light interact with it, which is pretty unbelievable. But I can give you an idea of how it works.
There's this device for light called an interferometer. You take a laser beam, you split it into two paths, and then you recombine it at a later point. And where it recombines, you put a beam splitter — a half-transparent mirror that sometimes lets light through and sometimes reflects it 90 degrees.
So there are two directions light can come out. But if the two paths are the same length, then when the beams get to the beam splitter, they cancel each other out in one direction, and they only come out in the other direction.
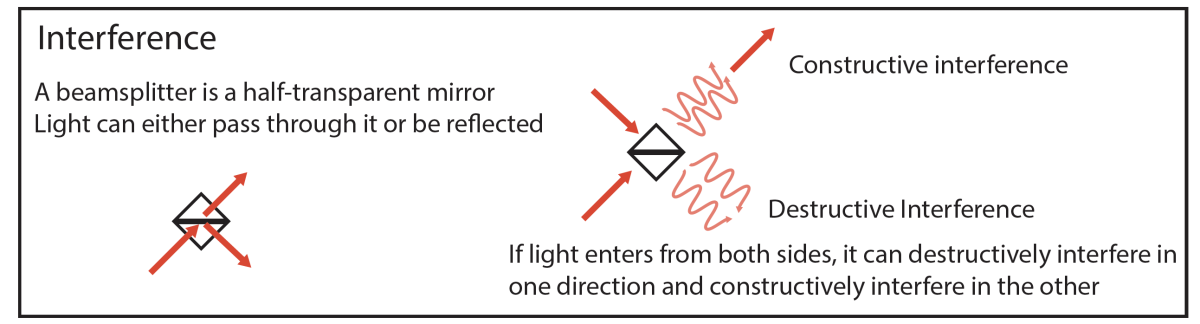
The weird quantum-mechanical part about this is, even if my laser is only sending a single photon at a time — so there's just one particle of light at a time — those particles still behave the same way. They can split and then interfere with themselves, even though there's only one photon at a time.
So if you send a single photon in, and that photon comes out the port where it wasn't supposed to, I know that one of the paths of the interferometer is blocked. I'm able to detect that there was something blocking one of the paths without having my photon actually run into it.
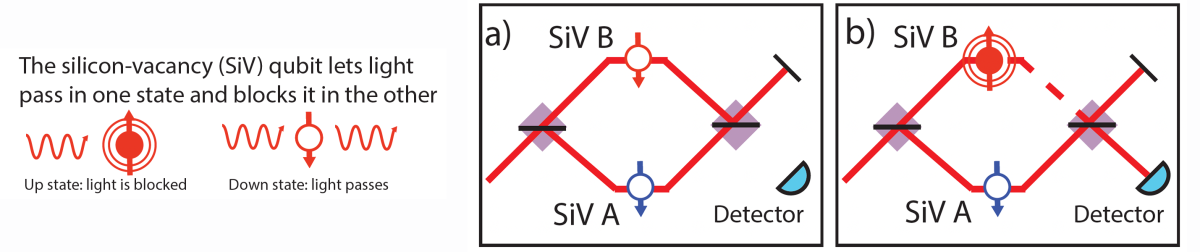
We basically we do that, except instead of having the light take two different paths, we split it in frequency. So you can build an interferometer where instead of traveling two paths, the light turns into two different frequencies, and then it gets recombined at a central one.
Q: How does that help you do secure communication?
DL: There are two vacancy centers, and based on their state they're going to be blocking light or letting light through. You send light in at those two frequencies, and then you combine it.
If both vacancies are letting light through, then the two paths interfere, and no light comes out at the combined frequency. And if both vacancies are blocking light, no light comes out at the combined frequency. But if one is letting light through, and one is blocking it, then light does come out at that central frequency.
So if you get light at that combined frequency, you know one was blocking and one wasn't blocking — but you don't know which one is which. And that process generates quantum entanglement between the two vacancies. You can now use one to talk to you and another one to talk to me.
For single quantum bits, if you measure them, you usually change them. So if there's some eavesdropper, they're going to change the bits that I'm sending to you. You can say, ‘Hey, here's the statistics on my information, here’s the statistics on your information.’ If the party in between is adversarial — if they're breaking the rules and just looking at our information and then computing stuff — they're not going to be able to push this statistic above a certain threshold. So as long as that number is higher than the threshold, we know they're not cheating, and our information is secure.




