Building quality software tends to follow a familiar routine for most developers. You write code on your computer within an integrated development environment (IDE), and then, to check for any security flaws, you upload it to a central repository and run a security scan. The results appear on a dashboard in your web browser, separate from the IDE.
Linghui Luo was asked to rethink this workflow during a five-month internship at Amazon Web Services (AWS) in 2020. In doing so, she came up with a prototype for a novel way to run security scans on code. The prototype became the basis for a 2021 research paper and evolved into the newly launched Amazon CodeGuru Security plugin for two IDEs, Amazon SageMaker Studio and Jupyter notebooks.
Luo joined Amazon full-time in early 2022 as an AWS applied scientist, shortly after earning her PhD in computer science at the Heinz Nixdorf Institute at Paderborn University in Germany. Now based in Berlin, she has continued her research into quicker, easier methods for ensuring code is stable and secure. The first line of her GitHub biography page says it best: “The usage of security analysis tools should become an industrial convention in secure software development. However, we need to create usable analysis tools first.”
Streamlining security scans
Luo's work makes it easier for developers to use Amazon CodeGuru Security, a tool that can identify critical issues, security vulnerabilities, and hard-to-find bugs. CodeGuru Security is a static analysis tool, which means it evaluates each line of code without running it, offering an opportunity to head off problems as work progresses.
But she doesn't just focus on the software — she also studies the developers who use it. The results affirm a key Amazon practice: working backwards from the customer.
CodeGuru Security operates in the cloud, which is ideal for static analysis tools — particularly ones that perform the kind of deep analysis that security testing requires. In the cloud, users can track and store issues in a central location, and each scan runs more efficiently than it would on a single machine.
When developers use popular continuous integration workflows, they receive security recommendations every time they push code. The recommendations appear in the developer’s web browser.
What if developers could have a direct line to CodeGuru Security, running static analysis in the cloud from within the IDE? This was the challenge AWS applied scientist Martin Schäf presented to Luo for her internship.
"At the beginning, most people would think this is a software engineering problem, but it's actually not," Luo said. "What we took was basically a user-centric approach."
Starting with the user
Luo first interviewed AWS developers to determine what they expected from an IDE-based static analysis tool. When should the analysis happen? How automated should it be? How long did they think it should take?
The problem may not be as straightforward as it sounds. While some tools already do static analysis from within an IDE, it is typically "lightweight" scanning that catches glaring problems and takes maybe 10 seconds at most to complete. Static application security testing, on the other hand, looks more intensively at the code. That takes several minutes, even with cloud resources — in the past, such testing was much slower, taking hours. A successful integration would need to manage user expectations on timing, among other aspects.
Based on her interviews with developers, Luo developed a prototype CodeGuru Security extension for Visual Studio, a popular IDE. Then she ran usability tests to see whether what she built matched developers' needs.
The project, Luo said, expanded her horizons in understanding how to build more useful tools for developers. Actions that may have seemed trivial to her, like needing to take code out of the IDE and upload it somewhere else for analysis, proved to be pain points for developers who wanted a static analysis integration to be as seamless as possible.
"As a PhD student who has always been at university, I had some assumptions about what developers would like to have," Luo said. "But after talking to them, I found out that what they want is totally different." The experience reinforced to her the importance of talking to users before you develop a tool.
Validating code from notebooks
The new CodeGuru plugin for Jupyter and SageMaker Studio is meant to help users prevent bugs from sneaking into code developed in notebooks. Data scientists like notebooks because they can append text and relevant images to lines of code.
But the platform can lend itself to reproducibility issues. Let's say you have four lines of code, each in a different code cell within a notebook. A user can run the code cells in arbitrary order; but when the code is shared, another user might run them in a different sequence. That’s an issue, because running code cells in a different order might produce different results. Luo offers the example in a recent paper about the issue co-authored with Amazon colleagues Schäf, Ben Liblit, Alejandro Molina Ramirez, Rajdeep Mukherjee, Goran Piskachev, Omer Tripp, and Willem Visser; along with Zachary Patterson of the University of Texas at Dallas.
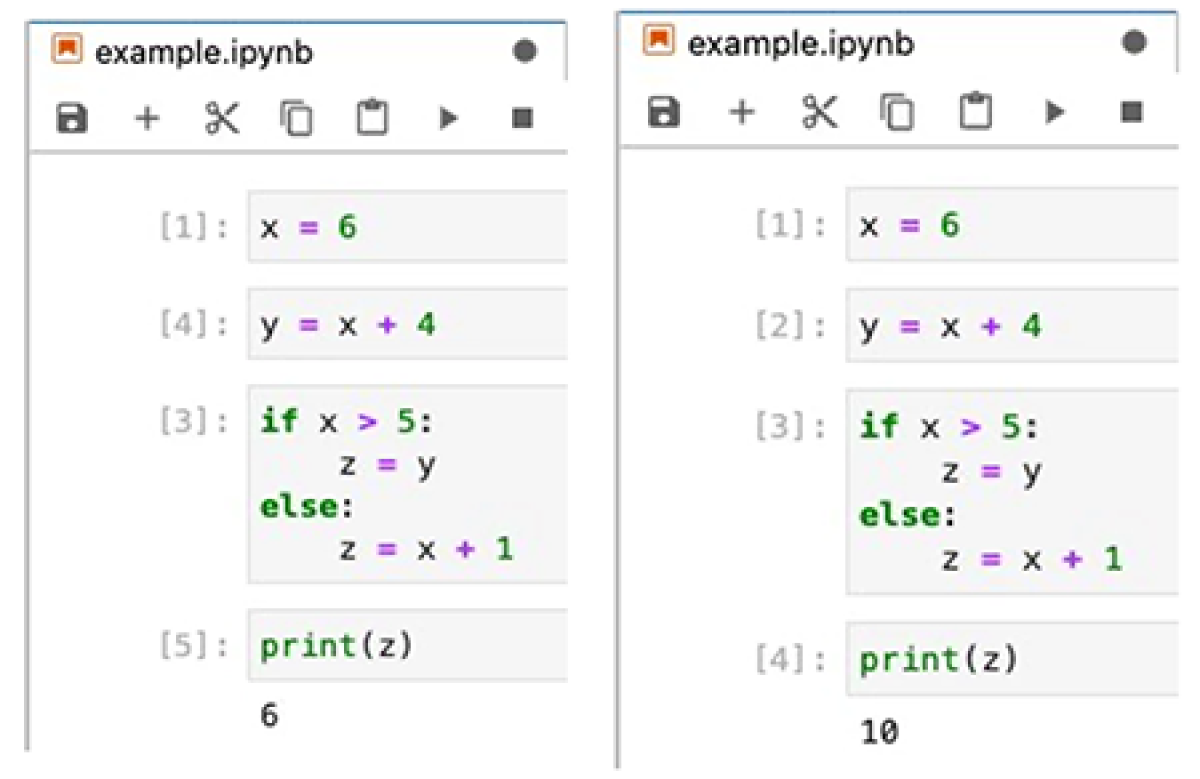
Notebooks are great for data exploration and presentation, Luo explained, but too often, the code gets passed on and deployed without being checked. "If you cannot reproduce the result, how can you ensure that your code is running correctly?" Luo said. The CodeGuru plugin can flag such potential flaws and suggest improvements.
Of course, a security recommendation is only truly useful if the developer actually deploys it. Ongoing research on Luo's team explores how to gauge the quality of static analysis rules by measuring certain developer actions.
Visible impact
Luo developed an interest in computers as a high school student in China. It was a "natural choice," she said, to go right into computer science for college. Her interest in computer security emerged from a personal experience while she was a master's student. She noticed that an app she was using allowed a user to change the cell phone number attached to an account without any verification. The app was connected to her bank, and she was appalled at how insecure it was. That realization led to her focus on software security during her doctoral program.
My team at Amazon is a good platform for me to be able to put science into production and have a visible impact in a short time.
Luo's initiative during her Amazon internship — and the openness of her team — made it possible to make the most of her time there. By the time her internship was done, she already had an offer to join the team full-time. Schäf, Luo’s hiring manager, noted that Luo owned the science work on the SageMaker plugin from start to finish.
“At Amazon, we are customer obsessed, which is why it is so important to have scientists like her that follow a good scientific process to help our engineers understand which solutions bring the best value to our customer,” he said. “She quickly turns ideas into prototypes that allow us to verify what benefits our customers and what doesn’t.”
Luo had considered staying in academia after earning her doctoral degree, and at one point she also received an offer to join a research institution in Germany as tenure-track faculty. But ultimately, she decided Amazon was the place for her.
"It was a really hard decision," she said. "But I always wanted to do more applicable science. My team at Amazon is a good platform for me to be able to put science into production and have a visible impact in a short time."